Quality Attributes
Non-functional requirements has three categories as given below.
1. Quality attribute
2. Business or strategic decisions
3. Constraints
In this blog we are going to have a detailed discussion about quality attributes.

Quality Attributes
In the software development life cycle quality attributes play a major role in the design, implementation, and development phases.
Business requirements are fulfilled with the quality attributes.
They are testable to fulfil the user requirements and satisfy them.
Classification of Quality Attributes.
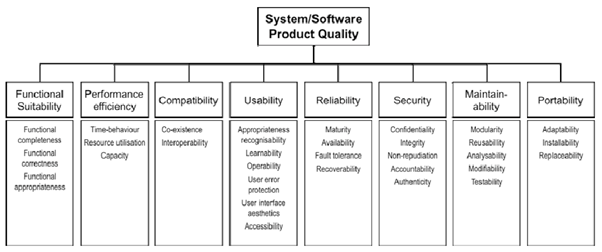
Quality attributes are categorized into 8 groups according to ISO 25010 Classification given below.
1. Functional Sustainability
2. Performance efficiency
3. Compatibility
4. Usability
5. Reliability
6. Security
7. Maintainability
8. Portability
Quality attributes has impact on another quality attribute.
When considering the life cycle of the system, these attributes relate with different phases.
Quality attributes are measurable with different factors.
Availability
The system should be available to its user when-ever they wanted to access the proper and working system and obtain its usage.
A system can be unavailable during the situations given below.
- Malicious attack.
- Failures in the infrastructures used.
- During maintenance è When a system is under maintenance it will be unavailable to its user during a particular time, therefore the user cannot access the system when they needed.
- Errors in the system.
- System load
- Poor internet connection.
- Power cut.
Modifiability
A system can be modified due to new requirements requested by the client or developer or the administrator.
The changes can be made possibly during the designing period or runtime or development phase. Modifications must be done with less cost as possible.
Modification cane be changing the technologies, or adding new functionalities to improve the system, changing the interface according to the situations (Christmas season) and changing the platform.
For an example, when the system is running in the windows operating system (OS) but needed to run in another OS like Linux, this is a new requirement. The developer should be able to modify the code by referring the documentation during the development time.
Interoperability
It is responsible to communicate with specific data and communication protocols, and operations of the system with external systems.
The system should get integrated with third party system to enhance the functioning of the system.
Interoperability is divided into two groups as mentioned below.
- Syntactic — Exchange data between two or more systems developed with same technologies. Communication is done by specified data and protocols.
- Semantic — Communicate and exchange data between different systems developed under different technologies. It should be able to interpret the information automatically and provide the result in a useful and meaningful manner.
Performance
Performance of the system is compared with a particular time duration. For an example when the system administrator needs to search a particular data, the system should have the capable to fetch them from the database within milliseconds.
If takes a longer time it will be considered as a failure in the performance of the system. To achieve the required performance certain functionalities must be changed.
Latency and throughput are the features which are considered under performance, comparing with the time.
Latency — Time taken to respond to an event.
Throughput — Number of events occurred within given time.
Reliability
The system should have the ability to provide the required services when one or more components of the system fails, when the hardware or software are damaged.
Reliability can be achieved by having a back-up service where the same data should be stored as redundant. This helps to avoid single point of failure.
Reliability is disturbed by availability, accuracy, and predictability.
Scalability
The system should be able to manage and provide its services effectively when the number of users or resources increases without reducing the performance of the system.
Scalability can be achieved by two ways as mentioned below.
1.Vertical Scaling — adding more resources like memory disk to a single server. Normally this can be reached faster to the limit of the machine.
2.Horizontal Scaling — Achieved by adding new servers. For parallel applications, the horizontal scaling is virtually limitless.
Example:
When there is an offer in the online shopping application, all the users try to access the relevant product within the given period to get the offer, therefore the system should have the capability to handle large number of purchases at that time without any failure.
Security
A system should have the ability to provide the services to its authorized users. Unauthorized access must be prevented to protect the data. Security can be achieved by encryption, authentication (authenticating a user by the password) and authorization (controlling the access).
Example:
In an online payment the transaction of money should be done in a highly secure manner. The data provided when doing online payment are confidential which has to be protected.
Testability
The system should be testable to find the defects and improve where necessary with the predefined sections.
During testing the system components are individually tested and later the system will be tested entirely.
Initial tests are done at the developing environment and the final test will be done at the environment. During the final test, the system has to be to check whether it fits to the environment and fulfil the user requirements.
Usability
Under usability the system gets compared with the Oss that can use the system, supported versions of the browser, hardware supported, support towards the disabled people, user friendly interfaces and user experiences.
Reusability
It is a feature used to save time and cost for the development team and to minimize the duplications (redundancy). Normally the duplications cannot be avoided, but it can be reduced. The available feature should be able to use in other sub-systems or the components.
Lets have a discussion about quality attribute scenario.
Quality Attribute Scenario (QAS)

Quality attributes are documented in a universal manner as Quality Attribute Scenario (QAS).
General scenarios (scenarios are more general) or the concrete scenarios (scenarios are more specific) are documented in this template.
This documentation describes the quality attributes in a measurable way to test them. Which means the quality attributes should have scales to obtain a final value to check the quality attributes.
Quality attributes are handled by the business analyst and the software architect.
Role of System architect on quality attributes — Software Architect analyses the quality attributes and priorities according to the need of the software proposed by the client.
QAS consists of 6 parts as mentioned below.
- Source
System or human being. It can be end user, developer, tester, administrator, operating system.
2. Stimulus
Actions involved by the source. It can be during CRUD (Create, Read, Update, Delete) functionality, search functionality.
3. Environment
When the stimulus should occur. It can be at run time, compile time, normal load, overload mode, online, offline, connected mode, disconnected mode.
4. Artifact
It can be the system or part of the system.
5. Response
It is about how the artifact responses of the system according to the stimulus(action)
6. Response measure
Quantitative measurement is considered.
Quality attribute tactic
It is a decision made on design (plan) to improve a quality attribute response. They are present in the architectural patters therefore implementation of tactics in not necessary.

The collection of tactics is called as architectural strategy.
To improve the quality attributes different tactics should be improved. Sometimes changing one quality attribute may reduce the functioning of other quality attributes or attributes. Therefore, software architect should consider each attribute when improving the functioning of a quality attribute.
Example:
Availability Tactics

Fault detection
- Ping/Echo
It is asynchronous.
It is like sending a message (ping) and getting a reply (echo) within a limited time under examination. If the reply is not obtained, then the notification is sent to the fault correction system to identify the fault.
Operate under defined processes.
Disadvantage — Poor performance due to network overhead and process overhead.
2. Heartbeat
A monitored process where a component periodically emits a heartbeat message and other components listen to it. It can carry data too. If there is no emitting of heartbeat massage from the component, the heartbeat originating component is assumed to be failed.
Operate under defined processes.
3. Exception
It is another method to identify faults. When a fault is identified it throws an exception as the normal exception.
Operate under a single process.
Advantage — performance and availability are good.
Disadvantage — Poor user Experience

References
- https://www.researchgate.net/publication/260835091_Engineering_Dependability_to_Embedded_Systems_Software_via_Tactics
- https://www.cs.unb.ca/~wdu/cs6075w10/sa2.htm
- https://sse.tongji.edu.cn/yingshen/course/SA2014Spring/slides/SA03Tactics.pdf
- https://www.slideshare.net/ahsanriaz10/availability-tactics
- http://www.cse.chalmers.se/edu/year/2009/course/DAT135_Software_Architecture/lib/10_QualityAttributes2.pdf
- https://people.ece.ubc.ca/matei/EECE417/BASS/ch05lev1sec2.html
